Virtual Account Authorization Mode
If the developer already has its own account system and wants to integrate Aqara devices to enrich its own IoT ecosystem, but does not want users to perceive two sets of accounts, namely the Aqara account and its own account, they can integrate the Aqara device SDK in their own APP which binds the Aqara device to the specified virtual account to realize the interconnection.
- Virtual account: refers to the virtual aqara account created through the interface, and the user can bind devices to the virtual account through the open SDK or implementation tools.
The sequence diagram of the authorization process is shown below.
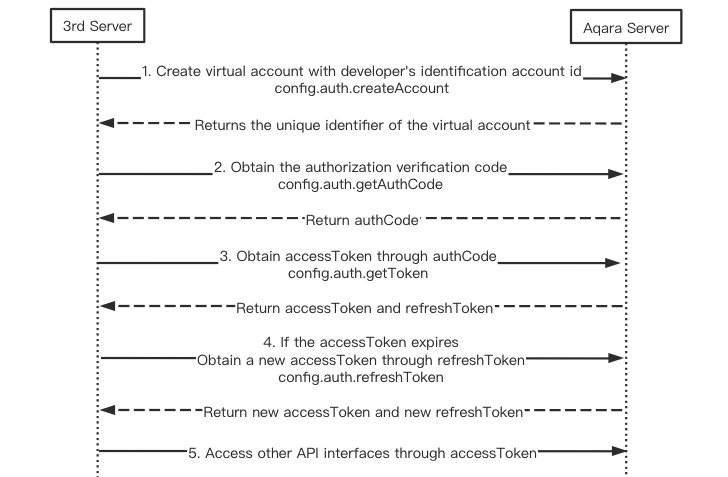
Step 1 Create an virtual account through developer's identification account id, and obtain the virtual user's unique identifier id ( openid)
- API intent: config.auth.createAccount
- Description: Create a virtual Aqara account through the provided developer ID(accountId) to realize the connection with the third-party account system. Virtual accounts cannot be used in the Aqara Home App, and need to be used with SDK.
- Request parameters
| Name |
Type |
Is required? |
Description |
| accountId |
String |
Yes |
The identity account id created by the developer is guaranteed to be unique under the appId |
| remark |
String |
No |
remark |
| needAccessToken |
Boolean |
No |
true: need to return accessToken; false: do not need to return accessToken |
| accessTokenValidity |
String |
No |
Access token valid time, default is 7d, support 1~24h (hour), 1~30d (day), 1~10y (year), the validity period of refreshToken is the access token’s expiration date plus 30 days |
{
"intent": "config.auth.createAccount",
"data": {
"accountId": "18900001234",
"remark": "lumi-1"
}
}
| Name |
Type |
Description |
| openId |
String |
virtual authorized user's unique identifier |
| expiresIn |
String |
The remaining valid time of the access token, the unit is s. Return when needAccessToken is true. |
| accessToken |
String |
Access token. Return when needAccessToken is true. |
| refreshToken |
String |
Refresh token, the validity period of refreshToken is the access token’s expiration date plus 30 days. Return when needAccessToken is true. |
{
"code": 0,
"requestId": "",
"message": "Success",
"msgDetails": null,
"result": {
"openId": "xxx"
}
}
Step 2 Obtain the authorization verification code through developer's identification account id
- API intent: config.auth.getAuthCode
- Description: This interface is used to obtain the authorization verification code. The verification code is valid for 10 minutes.
- Request parameters
| Name |
Type |
Is required? |
Description |
| account |
String |
Yes |
Developer's virtual account |
| accountType |
int |
Yes |
Account Type, 2-Virtual account |
| accessTokenValidity |
String |
No |
Access token valid time, default is 7d, support 1~24h (hour), 1~30d (day), 1~10y (year), the validity period of refreshToken is the access token’s expiration date plus 30 days |
{
"intent": "config.auth.getAuthCode",
"data": {
"account": "189000123456",
"accountType": 1,
"accessTokenValidity": "1h"
}
}
| Name |
Type |
Description |
| authCode |
String |
Return when accountType is 2. The authCode is valid for 10 minutes. |
{
"code": 0,
"requestId": "",
"message": "Success",
"msgDetails": null,
"result": {
"authCode": "xxxx"
}
}
Step 3 Obtain the accessToken through the authorization verification code
- API intent: config.auth.getToken
- Description: Before the authorization code expires, obtain the accessToken through the authorization code. The default validity period of the access token is 7 days, and the validity period can be customized through the "config.auth.getAuthCode" interface.
- Request parameters
| Name |
Type |
Is required? |
Description |
| authCode |
String |
Yes |
The authCode requested in the previous step |
| account |
String |
Yes |
Developer's virtual account. |
| accountType |
Integer |
Yes |
Account Type, 2-Virtual account |
{
"intent": "config.auth.getToken",
"data": {
"authCode": "xxxx",
"account": "xxx",
"accountType": 0
}
}
| Name |
Type |
Description |
| expiresIn |
String |
The remaining valid time of the access token, the unit is s. |
| openId |
String |
Authorized user's unique identifier |
| accessToken |
String |
Access token |
| refreshToken |
String |
Refresh token, the validity period of refreshToken is the access token’s expiration date plus 30 days. |
{
"code": 0,
"requestId": "",
"message": "Success",
"msgDetails": null,
"result": {
"expiresIn": "86400",
"openId": "593652793976837702248177061889",
"accessToken": "b8001e1893f5e4316a4f8c3b47df3720",
"refreshToken": "ddd9dc7e9ec7b772e852121ed2fe75aa"
}
}
Step 4 Refresh the accessToken through refreshToken to obtain new accessToken and refreshToken
- API intent: config.auth.refreshToken
- Description: Before the accessToken expires, refresh the access token with refreshToken through this interface. The refreshToken duration defaults to the period of accessToken + 30 days.
- Request parameters
| Name |
Type |
Is required? |
Description |
| refreshToken |
String |
Yes |
Refresh token |
{
"intent": "config.auth.refreshToken",
"data": {
"refreshToken": "xxxx"
}
}
| Name |
Type |
Description |
| expiresIn |
String |
The remaining valid time of the access token, the unit is s. |
| openId |
String |
Authorized user's unique identifier |
| accessToken |
String |
New access token |
| refreshToken |
String |
New refresh token |
{
"code": 0,
"requestId": "",
"message": "Success",
"msgDetails": null,
"result": {
"expiresIn": "86400",
"openId": "593652793976837702248177061889",
"accessToken": "b8001e1893f5e4316a4f8c3b47df3720",
"refreshToken": "ddd9dc7e9ec7b772e852121ed2fe75aa"
}
}
